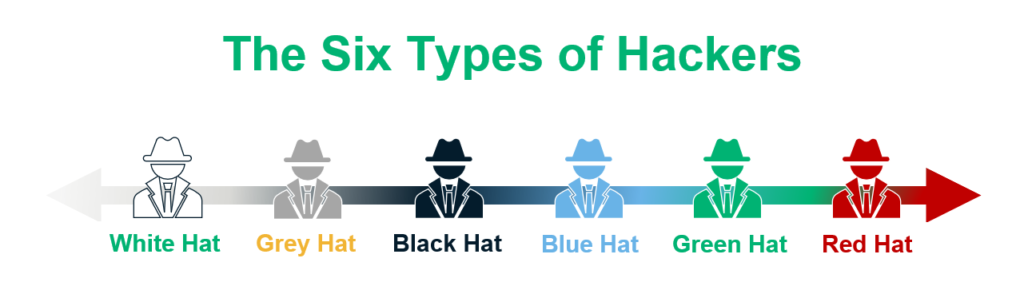
White hat Metasploit Project Exploit Computer security Penetration test, Framework, logo, payload png | PNGEgg
White hat Metasploit Project Exploit Computer security Penetration test, Framework, logo, payload png | PNGEgg
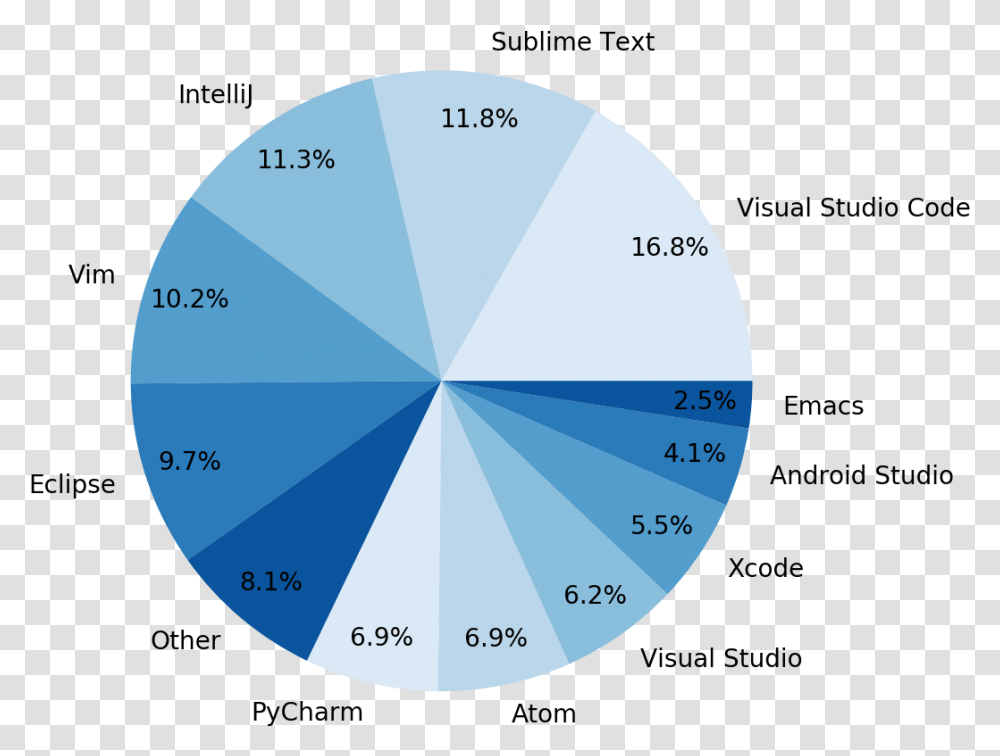
The Rise Of Microsoft Visual Studio Code Hacker Noon Visual Studio Code Market Share, Sphere, Diagram, Outer Space, Astronomy Transparent Png – Pngset.com

PDF) Overview of Ethical Issues such as security, confidentiality and Hacking in software engineering