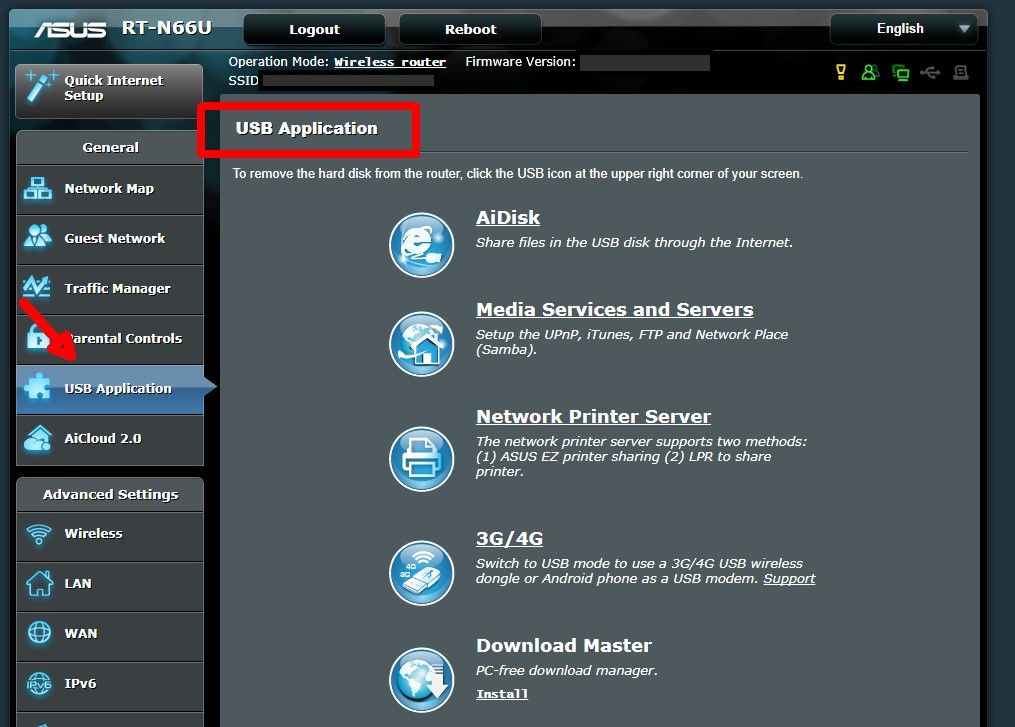
2012 top Hacking ASUS Routers via USB port Hacking Functionality into ASUSWRT Routers by Darell Tan Dec. 10, 2012 Asus routers support something they call a USB application, software that runs from a USB flash drive (see screen shot). One example ...

Con Watch: Why a Hacked Router Is “The Worst Thing That Can Happen to Computer Users” | The Saturday Evening Post

Index of /depository/authentication/Hacker can backdoor your computer and router in 30 seconds with $5 PoisonTap device _ Computerworld_files
Index of /depository/authentication/Hacker can backdoor your computer and router in 30 seconds with $5 PoisonTap device _ Computerworld_files