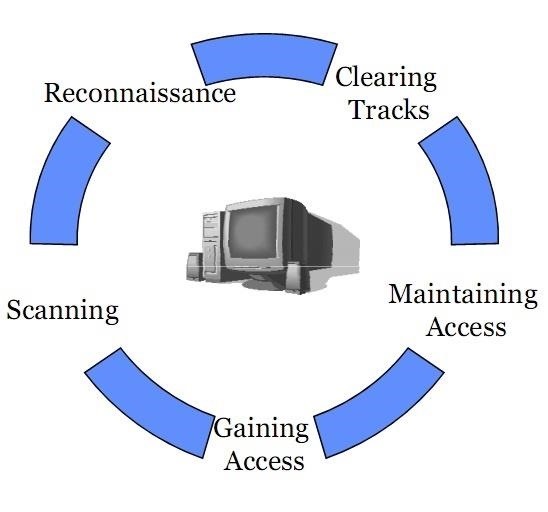
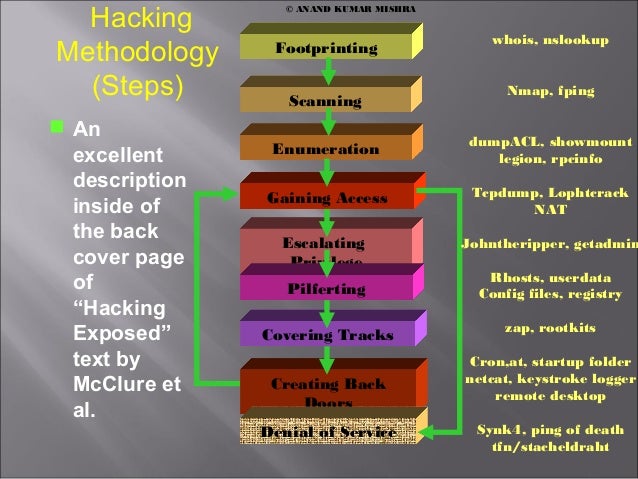
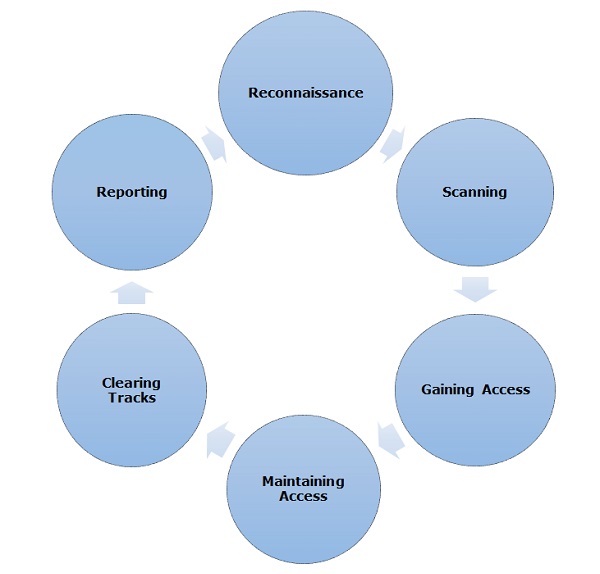
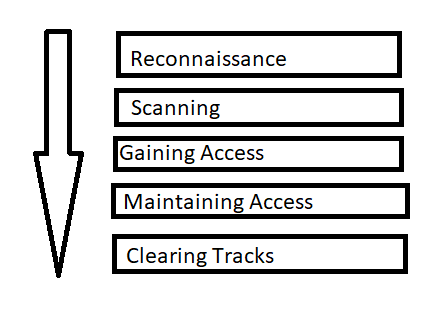
1 cs591 chow Hacking Methodology (Steps) An excellent description inside of the back cover page of “Hacking Exposed” text by McClure et al. Scanning Footprinting. - ppt download

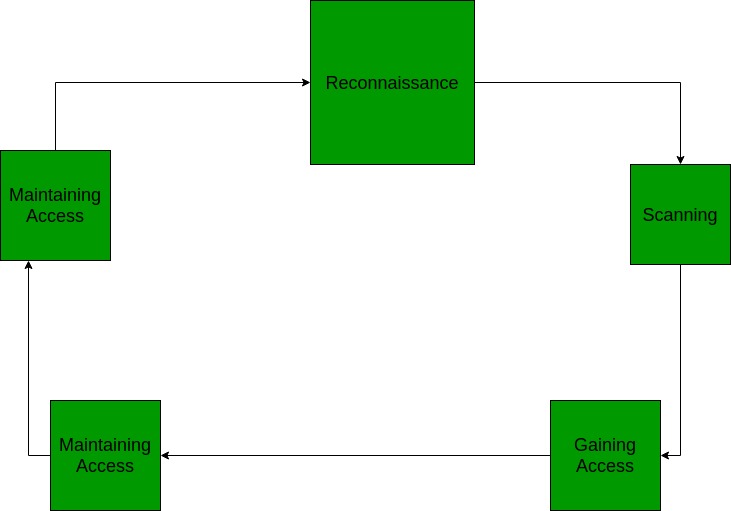
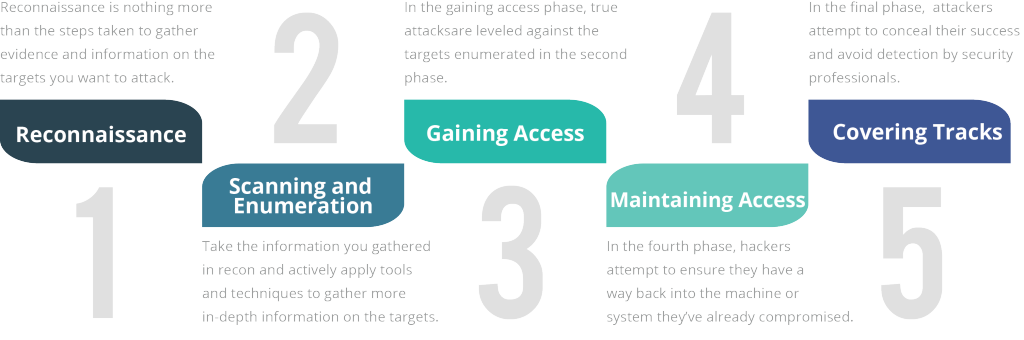
CEH Certified Ethical Hackers Society - Stages Of Ethical Hacking The below steps explain the different stages of hacking. Stage 1 - Reconnaissance: It is the act of gathering information related to